If your users’ computers experience a situation where BitLocker will not unlock their operating system drive, they must enter a recovery key, as mentioned earlier. You can store and access the keys using Intune.
To access the BitLocker key for a user, use the following procedure:
- In the Microsoft Intune admin center, navigate to Devices and select Windows devices.
- Locate the device in the list of Windows devices and then select it.
- In the navigation pane, select Recovery keys.
- In the details pane, select Show Recovery Key.
- Provide the key to the user to unlock their drive.
Implement and manage Microsoft Defender Credential Guard
When users sign in, they provide their user credentials via the Local Security Authority subsystem (LSA) to an authentication service. These user credentials are stored temporarily in memory in the LSA as hashes. Certain malicious software can access the LSA and exploit the stored hashes.
To help protect against this possibility, Windows 11 Enterprise and Windows 11 Education editions have a feature called Microsoft Defender Credential Guard, which implements virtualization-assisted security technology, enabling Microsoft Defender Credential Guard to block access to credentials stored in the Local Security Authority.
Requirements
In addition to requiring the appropriate edition of Windows 11, the following are the requirements for implementing Microsoft Defender Credential Guard:
- Support for Virtualization-based security.
- UEFI 2.3.1 or greater.
- Secure Boot.
- TPM 1.2 or 2.0, either discrete or firmware.
- UEFI (firmware) lock preferred.
- Virtualization features: Intel VT-x or AMD-V; SLAT must be enabled.
- Windows hypervisor, although Hyper-V doesn’t need to be installed.
Implement Microsoft Defender Credential Guard
After verifying that your computer meets the requirements, you can enable Microsoft Defender Credential Guard by using Group Policy or Microsoft Intune. To use Intune, perform the following steps:
- Open Microsoft Intune admin center.
- Navigate to Endpoint security and select Account protection.
- In the details pane, select Create Policy.
- On the Create a profile page, displayed in Figure 3-55, in Platform, select Windows 10 and later, and in the Profile list, choose Account protection.
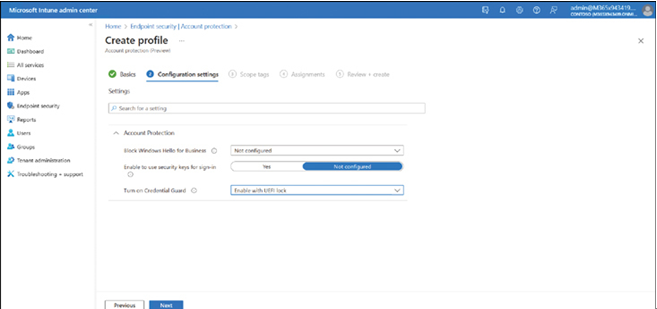
FIGURE 3-55 Enabling Microsoft Defender Credential Guard
- Click Create.
- In the Create profile wizard, on the Basics tab, enter a Name and Description and click Next.
- On the Configuration settings page, select Enable with UEFI lock in the Turn on Credential Guard list and click Next.
- Complete the wizard by defining scope tags and assignments and click Create on the Review + create page.
You can also use a configuration profile of type Endpoint protection:
- Select Devices, select Windows, and then select Configuration profiles.
- Select Create profile, and in the Platform list, select Windows 10 and later.
- In the Profile type list, select Templates.
- In the list of templates, select Endpoint protection, and click Create.
- On the Configuration settings page, expand Microsoft Defender Credential Guard and configure the desired settings.
Need More Review? Manage Microsoft Defender Credential Guard
To review further details about how Microsoft Defender Credential Guard works, refer to the Microsoft website at https://learn.microsoft.com/windows/security/identity-protection/credential-guard/credential-guard-manage.
