You can use Microsoft Defender Exploit Guard to help to reduce the attack surface of your users’ apps. Microsoft Defender Exploit Guard consists of four components:
- Exploit protection Uses Microsoft Defender Antivirus or, if installed, third-party antivirus software to help mitigate exploit techniques used against your organization’s apps.
- Attack surface reduction rules Uses rules to help prevent attack vectors implemented by scripts, email, and Office-based malware. Based on Microsoft Defender Antivirus.
- Network protection Extends Microsoft Defender SmartScreen protection in Microsoft Edge to other applications to prevent access to Internet domains that might host phishing scams, exploits, and other malicious content. Requires Microsoft Defender Antivirus and cloud-delivered protection enabled.
- Controlled folder access Helps protect against ransomware and malware by preventing changes to files in protected folders if the app attempting to make changes is malicious or exhibits suspicious behavior. It also requires Microsoft Defender Antivirus.
Note that different features are available in different Windows 11 edition, as shown in Table 3-15.
TABLE 3-15 Windows Defender Exploit Guard features
| Edition of Windows 11 | Features supported |
| Windows 11 Home | Exploit protectionControlled folder access |
| Windows 11 Pro | Exploit protectionControlled folder access |
| Windows 11 Enterprise E3 Windows 11 Education E3 | Exploit protectionControlled folder accessNetwork protection |
| Windows 11 Enterprise E5 Windows 11 Education E5 | Exploit protectionControlled folder accessNetwork protectionAttack surface reduction rules |
Exploit Protection
Exploit Protection helps to protect your users’ devices against malware that uses exploits to spread through your organization. Exploit Protection consists of a number of specific mitigations that you must enable and configure separately.
By default, Exploit Protection already enables several mitigations that apply to the operating system and specific apps. However, if you want to configure these and other mitigations, use the following procedure:
- Open the Windows Security app.
- Select the App & browser control tab.
- Scroll down and select the Exploit protection settings link.
- Configure the required settings on the Exploit protection page, shown in Figure 3-56. You can configure System settings and also specific Program settings. Review Table 3-16 for an overview of available settings.
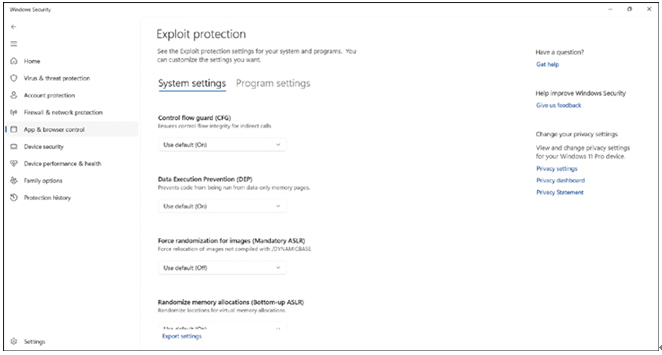
FIGURE 3-56 Configuring exploit protection settings
TABLE 3-16 Exploit protection mitigations
| Mitigation | Explanation |
| Control Flow Guard (CFG) | Control Flow Guard combats memory corruption vulnerabilities. |
| Data Execution Prevention (DEP) | Helps to prevent executable code from being run from pages that contain data. |
| Force Randomization For Images (Mandatory ASLR) | Helps prevent attacks by putting processes into memory at random locations. |
| Randomize Memory Allocations (Bottom-Up ASLR) | Helps prevent attacks by putting processes into memory at random locations. |
| High-Entropy ASLR | Helps prevent attacks by increasing variability when using Randomize memory allocations. |
| Validate Exception Chains (SEHOP) | Helps prevent the use of a structured exception-handler attack. |
| Validate Heap Integrity | Helps to prevent attacks that seek to use memory corruption. |
| Arbitrary code guard (ACG) | Prevents the introduction of non-image-backed executable code and prevents code pages from being modified. Optionally, it can allow thread opt-out and remote downgrade (configurable only with PowerShell). |
| Block low integrity images | Prevents the loading of images marked with Low Integrity. |
| Block remote images | Prevents loading of images from remote devices. |
| Block untrusted fonts | Prevents loading any GDI-based fonts not installed in the system fonts directory, notably fonts from the web. |
| Code integrity guard | Restricts loading of images signed by Microsoft, WHQL, or higher. Can optionally allow Microsoft Store signed images. |
| Disable extension points | Disables various extensibility mechanisms that allow DLL injection into all processes, such as AppInit DLLs, window hooks, and Winsock service providers. |
| Disable Win32k system calls | Prevents an app from using the Win32k system call table. |
| Do not allow child processes | Prevents an app from creating child processes. |
| Export address filtering (EAF) | Detects dangerous operations being resolved by malicious code. Can optionally validate access by modules commonly used by exploits. |
| Import address filtering (IAF) | Detects dangerous operations being resolved by malicious code. |
| Simulate execution (SimExec) | Ensures that calls to sensitive APIs return to legitimate callers. Only configurable for 32-bit (x86) applications. Not compatible with ACG |
| Validate API invocation (CallerCheck) | Ensures that legitimate callers invoke sensitive APIs. Only configurable for 32-bit (x86) applications. Not compatible with ACG |
| Validate handle usage | Causes an exception to be raised on any invalid handle references. |
| Validate image dependency integrity | Enforces code signing for Windows image dependency loading. |
| Validate stack integrity (StackPivot) | Ensures that the stack has not been redirected for sensitive APIs. Not compatible with ACG |
- Select the Export settings link to export the settings to an XML file.
- Distribute the XML file to other devices by using Microsoft Intune.
You can also enable mitigations in audit mode; this allows you to determine the effect of enabling a specific mitigation without affecting the user’s device usage.
Need More Review? Enable Exploit Protection
To review further details about enabling and configuring Exploit Protection, refer to the Microsoft website at https://learn.microsoft.com/en-gb/microsoft-365/security/defender-endpoint/customize-exploit-protection?view=o365-worldwide.
