To add a Microsoft Store app, use the following procedure:
- Open the Microsoft Intune admin center and select Apps in the navigation pane.
- Select All apps, and then select Add.
- On the Select add type blade displayed in Figure 4-2, in the App Type list, under the Store app heading, select Microsoft Store app (new) and click Select.
- On the Add App blade, select Search the Microsoft Store app (new).
On the Search the Microsoft Store app (new) blade, search for an app and then choose Select. as displayed in Figure 4-3.
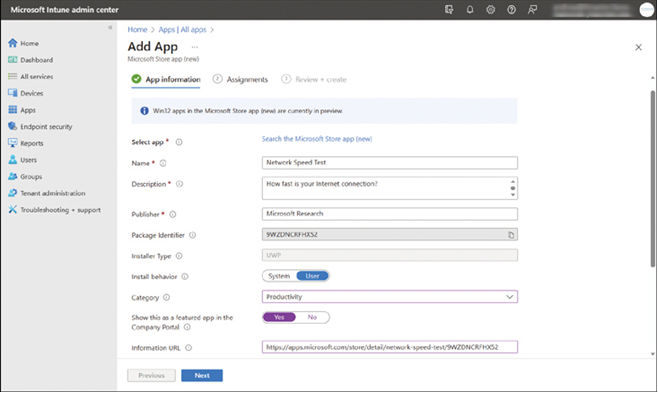
FIGURE 4-3 Adding a Microsoft Store app
To obtain the URL, visit the Appstore using a web browser, locate the app you want, and then copy the URL for the app’s page.
- Select Next, and on the Assignments tab select the appropriate groups for assignment, or select Add all users as displayed in Figure 4-4. Then select Next.
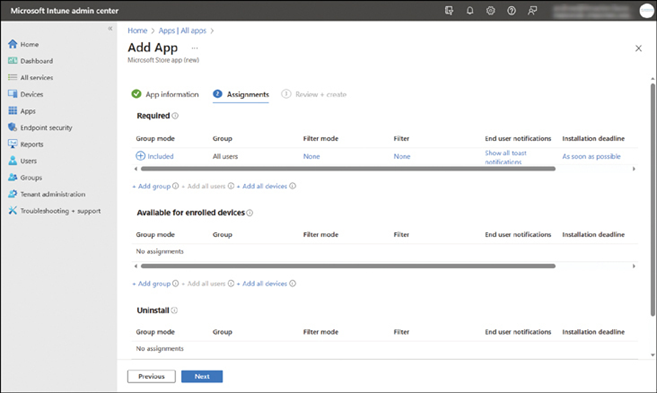
FIGURE 4-4 Assigning a Microsoft Store app
- On the Review + create tab, select Create.
After you create the app, you can use the Device install status and User install status options in the Monitor section to monitor the installation of the selected app.
Note Installing IOS and Android Store Apps
Installing store apps for iOS and Android is fairly similar to this process.
Note ARM64 APPS
Microsoft Store apps do not support any app with an ARM64 installer.
Configure Microsoft 365 Apps deployment by using the Microsoft Office Deployment Tool or Office Customization Tool (OCT)
You can configure Microsoft 365 Apps by using specialist tools that allow you to customize and configure the Office installation for your company’s needs. Two tools are available:
- Office Deployment Toolkit (ODT)
- Office Customization Tool
Using the Microsoft Office Deployment Tool
The ODT is a command-line utility that can deploy Microsoft 365 Apps to client devices. The ODT provides granular control over how to install Office installation. For example, you can configure the following:
- Which products are installed
- Language options
- Office updates
- Whether the install experience is displayed to users
Note ODT Download
You can download the ODT at www.microsoft.com/download/details.aspx?id=49117.
The installer file will create the setup.exe and the following sample configuration files:
- configuration-Office365-x64.xml
- configuration-Office365-x86.xml
- configuration-Office2019Enterprise.xml
- configuration-Office2021Enterprise.xml
The configuration-Office365-x64.xml sample configuration file looks like this: