You can configure Microsoft Defender Application Guard in one of two modes:
- Standalone Mode In standalone mode, users can manage their own device settings.
- Enterprise-Managed Mode With Enterprise mode, an administrator configures appropriate device settings using GPOs, MDM, or Windows PowerShell.
You can enable and configure Microsoft Defender Application Guard from Windows Security. However, to configure the relevant settings in Intune, use the following procedure:
- Open Microsoft Intune admin center.
- Navigate to Devices and then select Windows.
- Click Configuration profiles.
- Click Create profile.
- On the Create a profile page, select Windows 10 and later and then select Templates.
- In the list of templates, select Endpoint protection and click Create.
- Enter a Name and Description on the Basics tab, and then, on the Configuration settings page, expand Microsoft Defender Application Guard.
- As shown in Figure 3-58, select Enabled for Edge in the Application Guard list, and then configure supplemental settings, such as clipboard behavior and printing. Click Next.
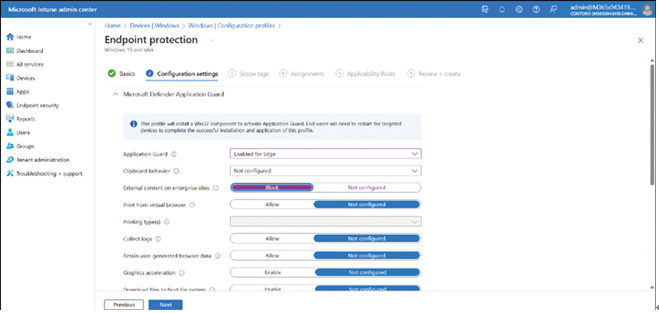
FIGURE 3-58 Enabling and configuring Application Guard
- Configure scope tags and assignments as necessary, and then choose Create to create the profile.
To use Microsoft Defender Application Guard in standalone mode, select the ellipsis button in Microsoft Edge and then select New Application Guard window, as shown in Figure 3-59. The Microsoft Defender Application Guard service starts, and then a new instance of Microsoft Edge opens.
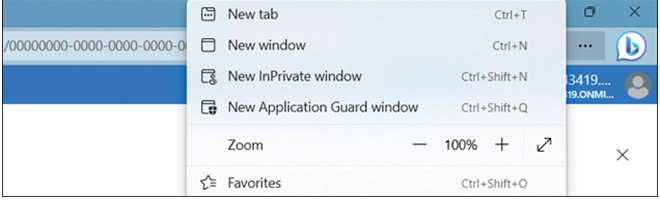
FIGURE 3-59 Opening a new Application Guard window
Need More Review? Configure Microsoft Defender Application Guard Policy Settings
To learn how to configure Microsoft Defender Application Guard policies, refer to the Microsoft website at https://learn.microsoft.com/windows/security/threat-protection/microsoft-defender-application-guard/md-app-guard-overview.
Implement Microsoft Defender Application Control
Microsoft Defender Application Control enables you to determine precisely which apps your users are allowed to run by blocking any unsigned apps and scripts. You configure Microsoft Defender Application Control with policies that specify whether a code that runs in kernel mode, such as device drivers or apps, can run.
A policy typically includes rules that
- Control options such as whether audit mode is enabled
- Determine whether user mode code integrity (UMCI) is enabled
- Specify the level at which apps are to be identified and/or trusted
Each Windows 11 device has a single Microsoft Defender Application Control policy defined for it. Typically, you configure this using GPOs in an AD DS environment or Intune for enrolled devices. Either way, the policy is stored as a local file called SIPolicy.p7b that resides in the C:\Windows\System32\CodeIntegrity folder; for UEFI-based computers, the file is <EFI System Partition>\Microsoft\Boot.