This section contains the solution to the thought experiment. Each answer explains why the answer choice is correct.
Scenario 1
- Microsoft Intune with Mobile Device Management enabled.
- Enable and configure Windows Autoenrollment.
- You require an Apple MDM Push Certificate for your organization.
Scenario 2
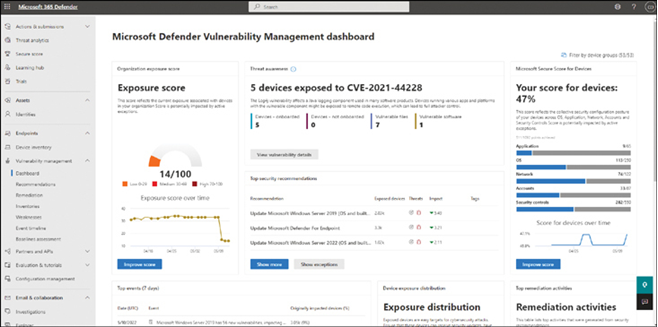
- You can monitor Threat Agent Status to determine the current status of Microsoft Defender on your users’ enrolled Windows devices.
- You can use the Microsoft Intune admin center to create an Endpoint Protection Profile that contains the necessary Microsoft Defender Application Guard settings and assign the profile to the appropriate group(s) of devices.
- In the Microsoft Intune admin center, create a Device Enrollment Restriction and define a Platform Restriction that prevents the enrollment of Android devices.
Scenario 3
- You should configure Delivery Optimization and select that updates are downloaded from Devices on my local network on all devices except one device which needs to receive the updates from the Microsoft update service.
- You can implement Delivery Optimization for the head office devices so that updates are received from other devices on the network. You can also configure bandwidth optimization measures that restrict the bandwidth consumed by updates during defined business hours.
- You should install Windows 11 Enterprise, version 22H2 (General Availability Channel), and then implement policy using Windows Update to defer Windows Feature Updates for the maximum allowed duration of 365 days.
- Enroll into the Windows Insider Program and install Windows 11 preview builds. Test these builds for compatibility issues. This should allow you to be ready to test the next General Availability Channel release and obtain compliance sign-off.
Scenario 4
1. You could implement Microsoft Tunnel for Intune. Microsoft Tunnel provides a VPN gateway for Android and iOS devices in your organization for access to on-premises resources.
- You must perform the following high-level steps:
• Create a server configuration on Intune.
• Create a site in Intune.
• Install a Microsoft Tunnel Gateway on a Linux server in your on-premises environment (by using an Intune script).
• Deploy the Microsoft Tunnel client app to your iOS and Android devices.
• Create and deploy VPN profiles to your iOS and Android devices.