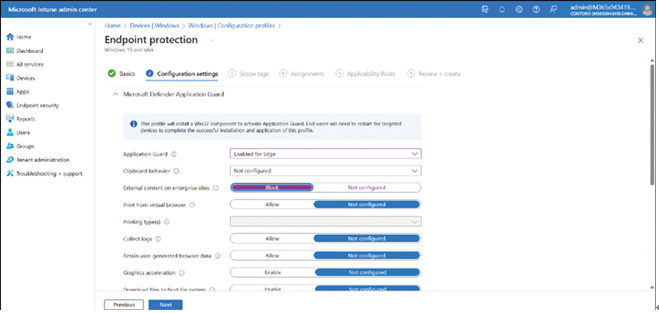
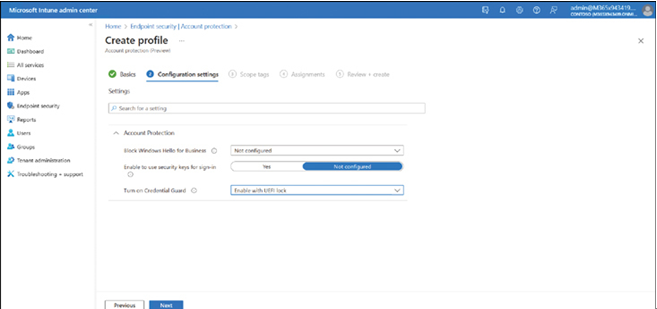
Malicious software can do many things to your computer, such as allowing unauthorized parties remote access to your computer or collecting and transmitting information that is sensitive or confidential to unauthorized third parties.
Some types of malware include:
- Computer viruses Replicating malware, normally with email attachments or files.
- Computer worms Replicate, without direct intervention, across networks.
- Trojan horses Trick the user into providing an attacker with remote access to the infected computer.
- Ransomware Harms the user by encrypting user data. A ransom (fee) needs to be paid to the malware authors to recover the data.
- Spyware Tracking software that reports to the third party how a computer is used.
The most common attack vector for malware is still by email, although attacks from websites, pirated software, video, and music files are becoming increasingly common.
You can help protect against malware infection by following these guidelines:
- All software should be from a reputable source.
- All software and operating system updates are applied.
- Antimalware software is installed and enabled on your devices.
- Antimalware definitions are up to date.
- Avoid using or accessing pirated software or media-sharing sites.
- Be suspicious of out-of-the-ordinary email attachments, and don’t open links in spam or phishing emails.
Although no antimalware solution can provide 100 percent safety, modern solutions can reduce the probability that malware compromises your device.
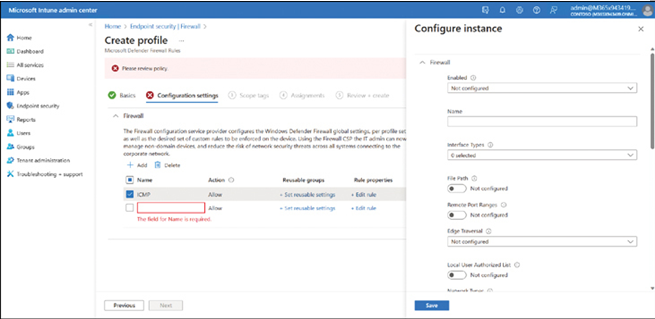
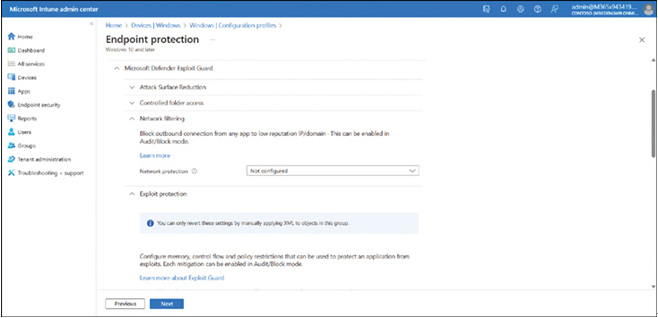
Microsoft Defender Antivirus can help protect your device by actively detecting spyware, malware, and viruses in the operating system and on Windows 11 installed on Hyper-V virtual machines. Windows Defender runs in the background and automatically installs new definitions as they are released, often daily.
You can use Microsoft Defender Antivirus manually to check for malware with various scan options listed in Table 3-18.
TABLE 3-18 Microsoft Defender Antivirus scan options
| Scan options | Description |
| Quick | Checks the most likely areas that malware, including viruses, spyware, and software, commonly infect. |
| Full | Scans all files on your hard disk and all running programs. |
| Custom | Enables users to scan specific drives and folders to target specific areas of their computers, such as removable drives. |
| Microsoft Defender Offline Scan | Allows users to find and remove difficult-to-remove malicious software. The system must reboot, and the scan can take about 15 minutes. |
You should routinely check your system for malware. If it becomes infected or you suspect malware is on your system, you can run a full scan.